Mcr Warrior
Veteran Member
- Joined
- 8 Jan 2009
- Messages
- 14,579
What a faff! But was this a scam, though?I once had my council tax messed up when new people moved in down the street and were somehow recorded as having moved into my property.
What a faff! But was this a scam, though?I once had my council tax messed up when new people moved in down the street and were somehow recorded as having moved into my property.
I think what is worrying me about my Virgin issue is could someone have tried using my Virgin account? I was told it was probably a mistake by the account department but Virgin would not elaborate further. They were quite unreassuring.What a faff! But was this a scam, though?
Quite possibly. But it could equally likely be a mistake with an address as something done with malice.I think what is worrying me about my Virgin issue is could someone have tried using my Virgin account?
That’s the thing, has someone hacked your account or have Virgin got their wires crossed and applied the details of another customer to your account by mistake? In my case it wasn’t a scam, I just mentioned it as a similar experience of the council getting their wires crossed and believing I’d moved when I hadn’t actually done so.I think what is worrying me about my Virgin issue is could someone have tried using my Virgin account? I was told it was probably a mistake by the account department but Virgin would not elaborate further. They were quite unreassuring.
No.Just had a call confirming my name and address as they wanted to check my loft and roof. I said I had recently moved and my new address was ... 24, Leinster Gardens, London W2.
Many of you will know what "building" that is.....!!
Thank you.
Was the message addressed to you by your correct name? Or maybe just 'Dear Subscriber' or some such?Just got an email claiming my ISP account needs updating. It was not very well done. It did start with the currently trendy "We hope this message finds you well".
I had an email yesterday claiming to be from Microsoft's "Outlook Team", saying that my Outlook account needed updating or it would be terminated as I "hadn't been responding to [their] messages".Just got an email claiming my ISP account needs updating. It was not very well done. It did start with the currently trendy "We hope this message finds you well".
The latter.Was the message addressed to you by your correct name? Or maybe just 'Dear Subscriber' or some such?
Was the message addressed to you by your correct name? Or maybe just 'Dear Subscriber' or some such?
The latter.
No 'probably' about it, hence the post here.Probably a scam. Probably best to report it as spam and then block the sender.
Wouldn't have spotted that in a million years.I was alerted to this ruse today.
To be fair, it makes sense to let the majority of the world's languages be equally represented on the Internet. Even western European languages haven't had their full alphabets represented - thinking of things like umlauts and other diacritical marks that aren't included in 7-bit US ASCII.Now they've allowed the use of other characters for web addresses (designed so the likes of Russia, Greece and Arab countries can have web addresses in their native language) that has opened up the use of characters that look like normal ones but aren't by scammers.
Of course it's a good idea, would be good for there to be some checking that a web address is not spoofing something else but I guess so many domains are registered each day to make that difficult, could build a database of banned addresses but that would be a lot of work.To be fair, it makes sense to let the majority of the world's languages be equally represented on the Internet. Even western European languages haven't had their full alphabets represented - thinking of things like umlauts and other diacritical marks that aren't included in 7-bit US ASCII.
Indeed, it would be an almost impossible task. I know that some larger corporations buy up the 'obvious' spoofs of their domains to stop scammers getting their hands on them.Of course it's a good idea, would be good for there to be some checking that a web address is not spoofing something else but I guess so many domains are registered each day to make that difficult, could build a database of banned addresses but that would be a lot of work.
Turning on two factor authentication is a huge yes. Make sure you also go through all the authorised apps and revoke access.Noticed on facebook *I've* been sending out spam/scam videos of products. Think there were four or five, anyhow deleted them and it looks like someone's hacked in from Kansas; changing password didn't help as they were apparently permanently logged in, so I found the procedure for logging out of every device including my android devices, changed password again, using two-factor log-in and hopefully whomever it was can't log in again.
If this happens again then I'm done with facebook! It takes some detective work to find the place where all your devices are logged in!
Yeah. Booking.com haven't admitted that there's a problem but there definitely is one. It's been going on for at least the last three to four months.New one on me this week, scam email received directly from a hotel through booking.com messaging! Apparently some hotels suffering hacks to their booking.com access.
Not a case of booking.yeah that their advert claims...New one on me this week, scam email received directly from a hotel through booking.com messaging! Apparently some hotels suffering hacks to their booking.com access.
Yes, this has been discussed by the security blogger Graham Cluley. Apparently the hacker makes a legitimate booking with a hotel, then sends them an attachment with additional "special requirements" for that booking. Unfortunately the attachment is booby trapped and installs malware (malicious software) on the hotel's computer, so that when they next log in their booking.com login details are snaffled and that's how the scammers are able to infiltrate the booking.com portal.New one on me this week, scam email received directly from a hotel through booking.com messaging! Apparently some hotels suffering hacks to their booking.com access.
 grahamcluley.com
grahamcluley.com
I’m speaking at an event in London in November, and needed to book a hotel room for the night before. I don’t normally use Booking.com for my travel arrangements, but on this occasion I did – and as a result I nearly fell for a scam that could have stolen my credit card details.
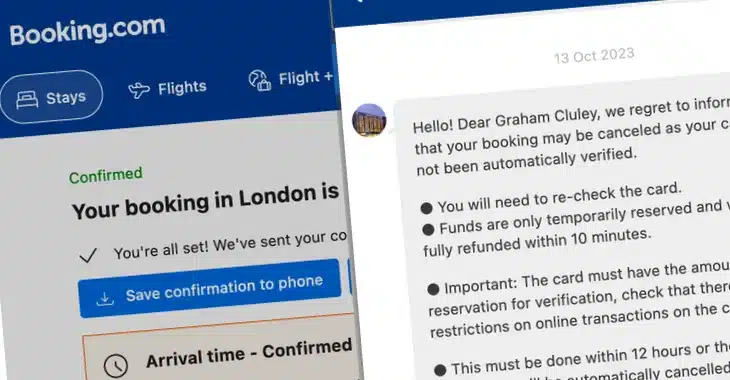
The online booking went smoothly as you would expect. But on Friday, two weeks after I made the original booking, I received a notification from the Booking.com smartphone app that I had a new message from the hotel I was planning to stay at.
I looked in the app, and sure enough I had a message from the “hotel”, straight after a legitimate message from the hotel. It also appears on the website version of Booking.com.
Fraudulent message appearing on Booking.com
Note that this wasn’t email spam. This was a message sent via the Booking.com website/app.Hello! Dear Graham Cluley, we regret to inform you that your booking may be canceled as your card has not been automatically verified.
● You will need to re-check the card.
● Funds are only temporarily reserved and will be fully refunded within 10 minutes.
● Important: The card must have the amount of the reservation for verification, check that there are no restrictions on online transactions on the card.
● This must be done within 12 hours or the reservation will be automatically cancelled.
● We recommend that you use a Mastercard in order to confirm.
« Please follow the link below to confirm your reservation »
Copy link if you can’t click on it
Regards © Booking 2023 Team
Here’s how it looked in the Booking.com smartphone app.
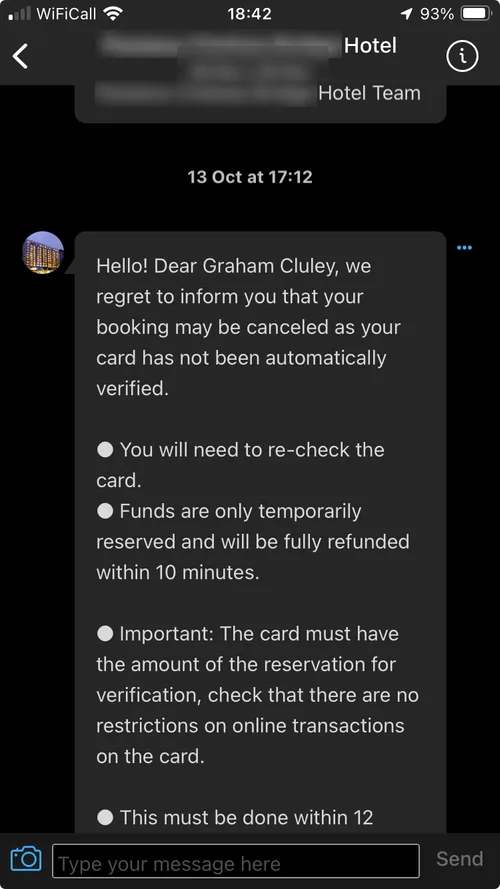
The message told me that my booking may be cancelled due to some credit card issue, and tells me to visit a URL to reconfirm my credit card details.
Clicking on the link took me to a webpage that contained my booking details, but was at a domain (com-id334112.com) that had been created just hours earlier. Sure enough, it asked me to enter my payment card data again.
After over 30 years of working in cybersecurity I like to think that I wouldn’t fall for a scam like this. But I received the notification when I was half-way down a supermarket aisle trying to find some aubergines. I could very easily have clicked on the link in my haste to ensure that I didn’t lose my hotel booking.
I can easily imagine how many Booking.com customers would fall for something like this, regardless of whether they were hunting for the ingredients for ratatouille or not.
I did the right thing. I went home, made a ratatouille, and then investigated how to contact Booking.com’s security team.
Unfortunately, Booking.com doesn’t have a “security.txt” file set up on its website listing how to contact it responsibly when a security issue has been found, which would have made things more straightforward.
Fortunately, colleagues in the security community on Mastodon, Twitter and other sites were able to point me in the right direction.
And so I sent the security team at Booking.com an email with all the details of what I had seen, in the hope that they would look into it and get back to me.
They haven’t responded to my email.
But this evening I (and I suspect other Booking.com customers) received the following email. Let’s take a look at what they say.
I'm not convinced that's how it works. The property never gets the guest's email address, they only see a randomised @booking.com address. All messages between the property and the guest go through Booking.com. If Booking.com are still allowing malware infected attachments through after all this time then I have to assume that they're in on it.Yes, this has been discussed by the security blogger Graham Cluley. Apparently the hacker makes a legitimate booking with a hotel, then sends them an attachment with additional "special requirements" for that booking. Unfortunately the attachment is booby trapped and installs malware (malicious software) on the hotel's computer, so that when they next log in their booking.com login details are snaffled and that's how the scammers are able to infiltrate the booking.com portal.
